Customer Background
A leading web agency managing a high-traffic WordPress site on Pressidium faced a critical challenge: implementing automated deployments without compromising Pressidium's stringent security measures. They needed a solution that offered both automation and robust security.
Challenge
The customer faced specific limitations with Pressidium's hosting environment:
- SFTP access was available (Pressidium SFTP Documentation)
- SSH command execution was restricted for security reasons
- Cache purging was necessary after deployments
Solution
We implemented a Zero Downtime Deployment strategy using DeployHQ with a custom cache purging mechanism through HTTP Post hooks.
1. DeployHQ Configuration
# DeployHQ Settings
---
server:
host: sftp.pressidium.com
port: 22
protocol: sftp
path: /public_html/wp-content/themes/custom-theme
excluded_files:
- .git
- node_modules
- .env
2. Cache Purging API Implementation
// wp-content/mu-plugins/cache-purge-api.php
<?php
add_action('rest_api_init', function () {
register_rest_route('cache-api/v1', '/purge', array(
'methods' => 'POST',
'callback' => 'handle_cache_purge',
'permission_callback' => 'verify_basic_auth'
));
});
function verify_basic_auth($request) {
// Get the Authorization header
$auth_header = $request->get_header('Authorization');
if (!$auth_header || strpos($auth_header, 'Basic ') !== 0) {
return false;
}
// Extract credentials
$credentials = base64_decode(substr($auth_header, 6));
list($username, $password) = explode(':', $credentials);
// Compare with configured credentials
return $username === defined('CACHE_API_USER') ? CACHE_API_USER : '' &&
$password === defined('CACHE_API_PASS') ? CACHE_API_PASS : '';
}
function handle_cache_purge($request) {
if (function_exists('pressidium_purge_cache')) {
pressidium_purge_cache();
return new WP_REST_Response(['status' => 'success'], 200);
}
return new WP_REST_Response(['status' => 'error'], 500);
}
3. Configuration in wp-config.php
// wp-config.php
define('CACHE_API_USER', 'your-username');
define('CACHE_API_PASS', 'your-secure-password');
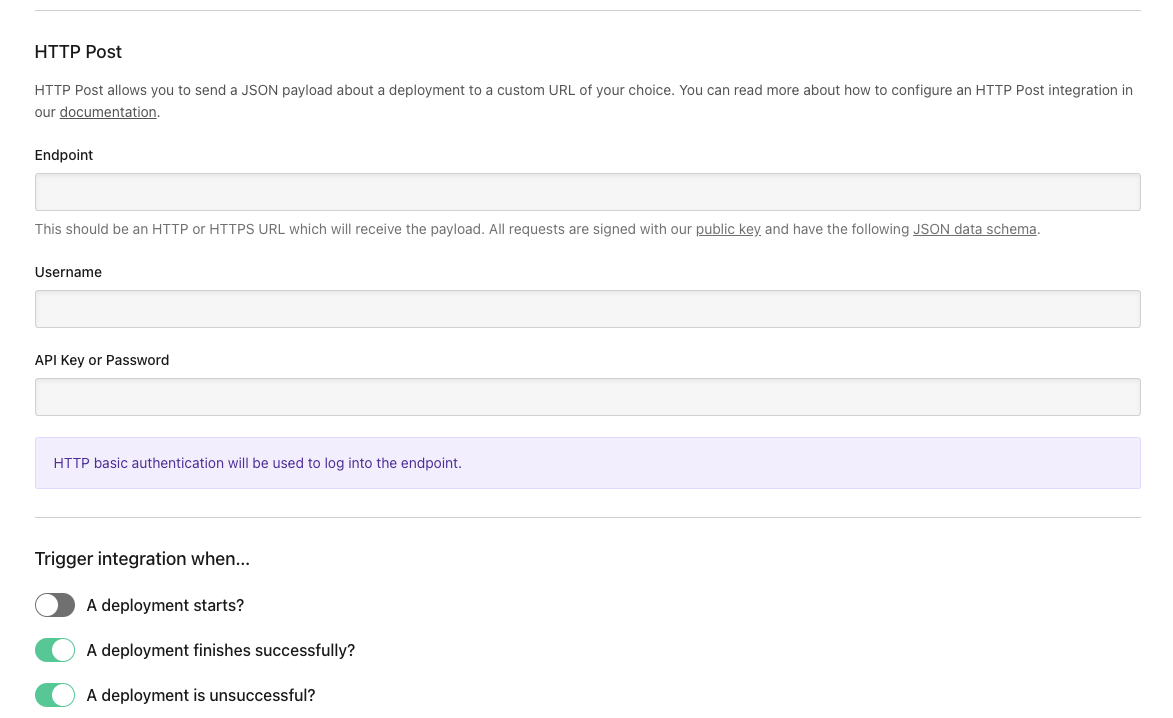
4. DeployHQ Post-Deploy HTTP Hook
In DeployHQ's project settings:
- Navigate to Integrations → HTTP Post
- Add new hook with:
URL: https://your-site.com/wp-json/cache-api/v1/purge
Username: your-username
Password: your-secure-password
5. Testing the Endpoint
You can test the endpoint using curl:
curl -X POST \
-u "your-username:your-secure-password" \
https://your-site.com/wp-json/cache-api/v1/purge
Results
The implementation achieved:
- Zero-downtime deployments via SFTP
- Secure cache purging through WordPress REST API
- Automated deployment workflow
- No need for SSH command execution
Benefits
- Maintained security compliance with Pressidium
- Automated deployment process
- Minimal deployment downtime
- Secure cache purging mechanism
Technical Details
Security Considerations
- REST API endpoint protected by basic authentication
- HTTPS encryption for all API calls
- Secure key storage in
wp-config.php
Implementation Steps
- Configure DeployHQ SFTP deployment
- Install cache purging API code
- Configure
wp-config.phpwith basic auth - Set up DeployHQ post-deploy hook
Conclusion
This solution successfully worked around Pressidium's SSH restrictions while maintaining a robust deployment process with automated cache purging.
Related Documentation
This case study demonstrates how to implement automated deployments within hosting restrictions while maintaining security and performance.
